News: Project Zero Finds iPhone & Android Open to Bugs in Broadcom's Wi-Fi Chips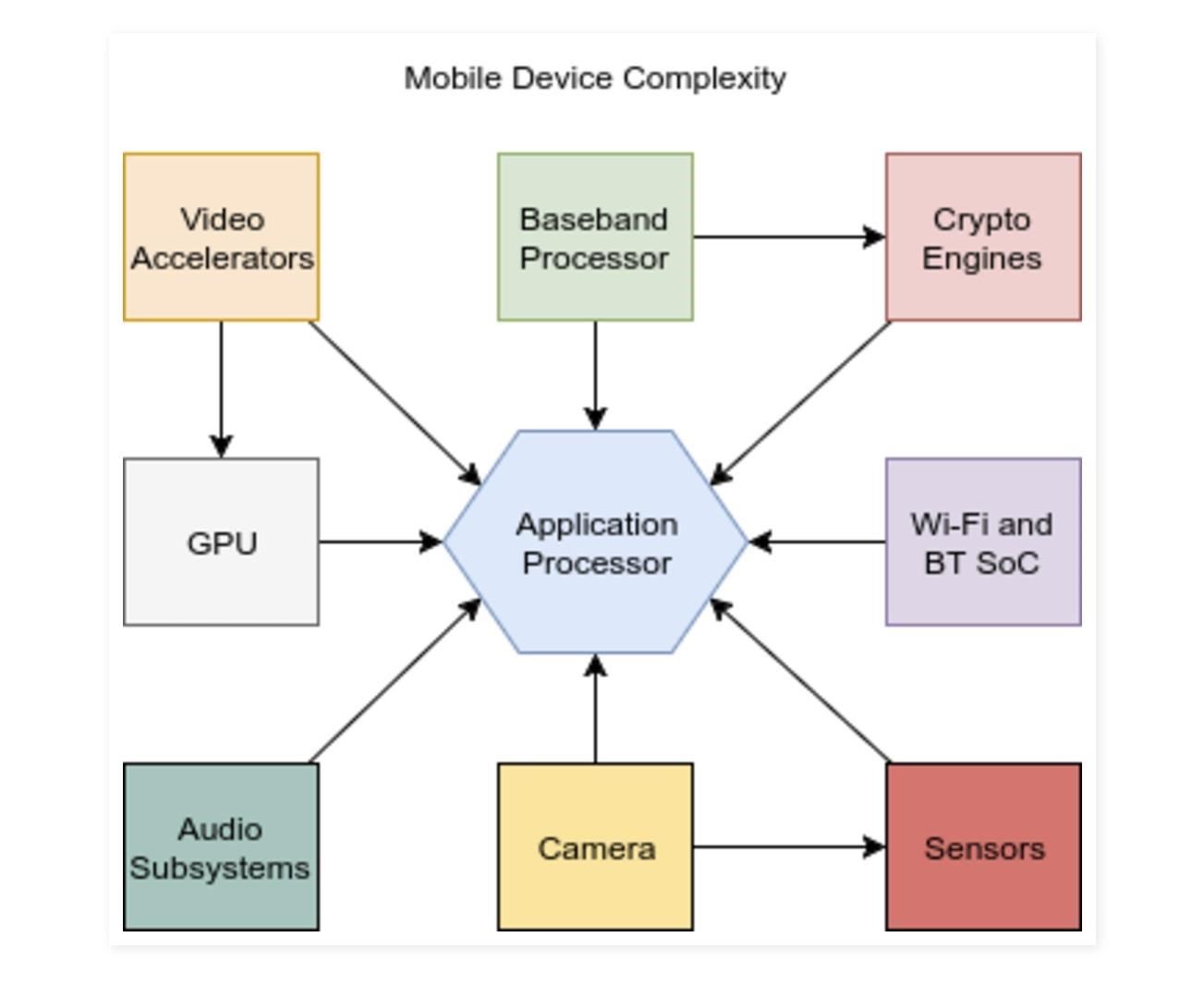
No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.Most iPhone and Android phones run on a Broadcom Wi-Fi system on a chip (SoC). Google's security researcher Gal Beniamini found a number of bugs on these SoCs, which affect the iPhone 4 all the way through to the iPhone 7, most of Google's Nexus handsets, and almost all Samsung Galaxy devices.The bugs don't stop there, either. Beniamini went on to note that Wi-Fi routers can be easy targets, too, so both sides of your phone's wireless internet connection could be vulnerable to theoretical attacks.Don't Miss: What You Should Know About the New 'Chrysaor' Android MalwareAndroid has done a lot of work to patch up its security system within the last year. Apple has also gone to great lengths to keep its systems secure, but this is where Beniamini says attackers found an opportunity to "pick the path of least resistance."Broadcom's Wi-Fi chips were the most attractive and easy target for an attacker to get past an iOS or Android security system, because Broadcom is the most commonly-used Wi-Fi SoC for mobile devices. Wi-Fi chips run on extremely complex code—complex enough that they are susceptible to vulnerabilities that an attacker could use to sneak by without ever being detected by the phone's user.According to Beniamini in his blog post on Broadcom's Wi-Fi stack:We've seen that while the firmware implementation on the Wi-Fi SoC is incredibly complex, it still lags behind in terms of security. Specifically, it lacks all basic exploit mitigations - including stack cookies, safe unlinking and access permission protection (by means of an MPU). Image via Project Zero Two actual exploits that utilized the bug were triggered in Broadcom's Wi-Fi SoC when connecting to networks that allow wireless roaming. According to ZDNet, "one occurred during the handling of the IEEE 802.11r Fast BSS Transition Feature's authentication response, while the other can be triggered when Cisco's proprietary CCKM Fast and Secure Roaming feature parsed a reassociation response."Don't Miss: Your Android Apps Are Secretly Getting Chatty with Your DataThe attacker was able to trigger vulnerabilities within Broadcom's code simply by being on the same Wi-Fi network as the targeted phone. Beniamini was then able to backtrack and look for what he calls "tags," which are chunks of data, or "Information Elements" (IEs) within the Wi-Fi management system:The presence of the 802.11r FT feature is indicated by the "fbt" tag. Similarly, support for CCKM is indicated by the "ccx" tag. Unfortunately, it seems that the Nexus 6P supports neither of these features. In fact, running a quick search for the "ccx" feature (CCKM support) on my own repository of Android firmware images revealed that this feature is not supported on any Nexus device, but is supported on a wide variety of Samsung flagship devices, a very partial list of which includes the Galaxy S7 (G930F, G930V), the Galaxy S7 Edge (G935F, G9350), the Galaxy S6 Edge (G925V) and many more.While combing through the firmware repository, Beniamini found two other tags with the name "Tunneled Direct Link Setup" (TDLS). TDLS is a connection that allows you to share data with other people on a Wi-Fi network, similar to how AirDrop works on the iPhone, but most importantly for us here, this means that TDLS is a vulnerability that can be hacked into.While researching TDLS, noted in the Wi-Fi firmware as "betdls" and "tdls" tags, Beniamini concluded that the attackers were able to leverage these bugs by exploiting TDLS vulnerabilities within the Wi-Fi SoC code as "a vast majority of devices do, indeed, support TDLS. This includes all recent Nexus devices (Nexus 5, 6, 6P) and most Samsung flagships."Ultimately, the three companies are working to plug up all the holes. Beniamini patched up the vulnerabilities for iOS 10.3.1 for iPhone users, and also alerted Google. Broadcom is also working on fixing the vulnerabilities within its systems to prevent an attacker from executing code on its Wi-Fi chip, so stay on the lookout for firmware updates for both your phone and your router.Don't Miss: The 4 Best Phones for Privacy & SecurityFollow Gadget Hacks on Facebook, Twitter, Google+, and YouTube Follow Apple Hacks on Facebook, Twitter, and Pinterest Follow Android Hacks on Facebook, Twitter, and Pinterest Follow WonderHowTo on Facebook, Twitter, Pinterest, and Google+
Cover image via Kaboompics/Pixabay
Report Ad
Free Shipping Available. Buy on eBay. Money Back Guarantee!
Hi, you're watching VisiHow. Today I'm going to show you how to switch between satellite and terrain view on Google Maps on an iPhone 6.
Download Google Maps on a BlackBerry | HowStuffWorks
How To: Need a Place to Store Your Bike? Try One of These Cheap and Simple DIY Bicycle Racks The Future Is Near: Flying 45 MPH Hover Bikes Just a Few Years Away News: PVC KartCross Car - Pedaled Car from PVC Pipe News: Super Cool Pedal Powered PVC Car
How to Make a hovercraft « Hacks, Mods & Circuitry :: Gadget
Instagram 101: The Quickest Way to Like All Photos in Your
If you exceed your monthly mobile data limit, your cell phone bill can skyrocket pretty quickly. This is why a lot of people vigilantly monitor internet usage and even uninstall apps that use too much background data. Don't Miss: 10 Tricks for Conserving Data on Android
How to Stop Apps From Using Cellular Data On Android Phone
Streaming video won't stream if you're away from an Internet connection. Here's how to download audio from YouTube or an any other streaming video for offline listening.
YouTube Downloader - Download Video and Audio from YouTube
I am trying to unlock my Palm Centro from Sprint. I already did the cricket process and some others you have here. But I am still connecting to the Sprint Provisioning, I even tried to delete the Service but it did not let me. i know, I know, it wont let me do it, but I was desperate.
SOLVED: My palm centro will not connect to the internet, - Fixya
In this way, the EFS or IMEI loss is deeply related with what you do after rooting your Samsung Galaxy device. Keeping this thing in mind most of our ROM developers insert a script that automatically creates a backup of the EFS data on the external SD Card so that you might restore it back in case of loss or corruption.
How to Backup / Restore EFS Partition [IMEI] for Galaxy S3
How to Use a Bluetooth Device. Bluetooth is a wireless technology that has been around for over 20 years. It allows multiple devices to connect, interact, and sync without needing to set up complex networks and passwords.
May 09, 2018 · Your smartphone is a helpful travel companion. Before taking it abroad, here's a list of things to pack and do to ensure a problem-free trip.
iPhone International Travel Tips - TripIt Blog
Apple's scheduled to show off the first look of iOS 13 at WWDC 2019 on June 3, but what will the new operating system hold for iPhone? Rumors suggest that many features initially planned for iOS 12 will show up in iOS 13, codenamed "Yukon," and dark mode will be the big ticket item this […]
Flipboard: News: Features We Want in iOS 13 for iPhone
How to turn off (or turn on) landscape mode on the iPhone 6
With Hearthstone's latest expansion, The Witchwood, arriving on April 12 2018, Blizzard also rolled out a number of in-game improvements alongside Update 11.0.One improvement that could revolutionize the Friendly Challenge experience is deck sharing, allowing you and your friends to borrow each other's decks.
Hearthstone is about to let you borrow your friends' decks
The UCSC Genome Browser is a public, freely available, open source web-based graphical viewer for the display of genome sequences and their annotations. See
Mouse strain assembly hub - May 3, 2017 - UCSC Genome Browser
hgdownload.soe.ucsc.edu/hubs/mouseStrains/hubIndex.html
Mouse strain assembly hub - May 3, 2017. This assembly hub contains 16 different strains of mice as the primary sequence, along with strain-specific gene annotations. Viewing this assembly hub on mm10, there will be a multiple alignment between the reference and 16 different strains of mice plus rat.
UCSC Genome Browser Store
0 comments:
Post a Comment